So you want to use a BusKill style setup with your Yubikey while retaining all the Yubikey's functionality on your Qubes laptop...
Overview
In this post, I'll walk you through exactly how to emulate my setup. In a future post, I'll dive deep in to the mechanics of the setup and why I made the choices I made.
At the end of this post we will have a setup that;
- Retains all the Yubikey's original functionality. I will still use it as a second factor for logging in to my Qubes laptop and still be able to attach it to various qubes that require access to the yubi for things like SSH, GPG and U2F.
- Creates a mechanism to arm and disarm the BusKill functionality via keyboard shortcut and udev rules.
- When armed, removing the Yubikey will result in the system performing a soft shutdown.
The inspiration for this guide is a direct product of Michael Altfield's article:

Before you get started
These changes are dangerous and could put your system in to an unusable state. Please be comfortable with rescuing a Qubes system before tyring this:

Modify either sys-usb or disposable vm template
In this section we will add the scripts and udev rules that will listen for yubikey removals. If you've installed your Qubes system recently (>=4.1) it's likely your sys-usb qube is completely disposable.

If this is the case then you'll need to make all changes in your disposable template. In my case this was debian-11-dvm. If your sys-usb qube is NOT disposable then you can make these changes in the sys-usb qube itself.
Create the udev rules files
cd /rw/config
sudo touch buskill.rules buskill.rules.arm buskill.rules.disarm detect.rules
cat << EOF | sudo tee /rw/config/buskill.rules.arm
ACTION=="remove", SUBSYSTEM=="usb", ENV{ID_VENDOR}=="Yubico", RUN+="/usr/bin/qrexec-client-vm dom0 buskill.softShutdown"
ACTION=="remove", SUBSYSTEM=="input", ENV{ID_VENDOR}=="Yubico", RUN+="/usr/bin/qrexec-client-vm dom0 buskill.softShutdown"
ACTION=="remove", SUBSYSTEM=="usb", ENV{ID_VENDOR_FROM_DATABASE}=="Yubico.com", RUN+="/usr/bin/qrexec-client-vm dom0 buskill.softShutdown"
EOF
Copy/Paste the following in to /rw/config/detect.rules
ACTION=="add", SUBSYSTEM=="input", ENV{ID_VENDOR}=="Yubico", RUN+="/home/user/arm.sh"Modify /rw/config/rc.local so that the above rules get sym linked to /etc/udev/rules.d every time the qube starts.
cat << EOF | sudo tee --append /rw/config/rc.local
sudo ln -s /rw/config/buskill.rules /etc/udev/rules.d/ >> /rw/config/rc.local
sudo ln -s /rw/config/detect.rules /etc/udev/rules.d/ >> /rw/config/rc.local
sudo udevadm control --reload >> /rw/config/rc.local
EOFCreate scripts in the home directory of your disposable dvm template that will arm and disarm our system.
Create a script called /home/user/arm.sh that will contain
#!/bin/bash
sudo cp /rw/config/buskill.rules.arm /rw/config/buskill.rules
sudo udevadm control --reload
su - user -c "notify-send -t 5000 'Bus Kill' 'Armed'"Create a script called /home/user/disarm.sh that will contain
#!/bin/bash
sudo cp /rw/config/buskill.rules.disarm /rw/config/buskill.rules
sudo udevadm control --reload
notify-send -t 5000 "Buskill" "Disarmed for 15 seconds"
sleep 15
/home/user/arm.shThe disarm.sh script will only disarm the system for 15 seconds
Create a script called /home/user/disarm-perm.sh that will disarm the system until rearmed
#!/bin/bash
sudo cp /rw/config/buskill.rules.disarm /rw/config/buskill.rules
sudo udevadm control --reload
notify-send -t 5000 "Buskill" "Disarmed Permanently. Run arm.sh to rearm"Make all executable: chmod +x arm.sh disarm.sh disarm-perm.sh
Create a script in personal qube that will modify dom0
Create the following script inside of a trusted VM. For example your personal vm. The intent here is to create a script that dom0 will be able to pull out since you can't copy/paste in to dom0
nano dom0.sh
#!/bin/bash
sudo touch /etc/qubes-rpc/buskill.softShutdown
cat << EOF | sudo tee --append /etc/qubes-rpc/buskill.softShutdown
sudo shutdown -h now
EOF
sudo chmod 755 /etc/qubes-rpc/buskill.softShutdown
sudo touch /etc/qubes-rpc/policy/buskill.softShutdown
cat << EOF | sudo tee /etc/qubes-rpc/policy/buskill.softShutdown
sys-usb dom0 allow
EOF
sudo chmod 644 /etc/qubes-rpc/policy/buskill.softShutdown
touch ~/arm.sh
chmod 755 ~/arm.sh
echo "qvm-run sys-usb /home/user/arm.sh" >> ~/arm.sh
touch ~/disarm.sh
chmod 755 ~/disarm.sh
echo "qvm-run sys-usb /home/user/disarm.sh" >> ~/disarm.sh
touch ~/disarm-perm.sh
chmod 755 ~/disarm-perm.sh
echo "qvm-run sys-usb /home/user/disarm-perm.sh" >> ~/disarm-perm.shchmod 755 dom0.sh
Inside of dom0 terminal run
qvm-run --pass-io personal 'cat /home/user/dom0.sh' > dom0.sh
chmod +x dom0.sh
./dom0.shCreate keyboard shortcuts to arm and disarm your system
Settings -> Keyboard you will set up keyboard shortcuts to trigger the arm.sh and disarm.sh scripts in dom0
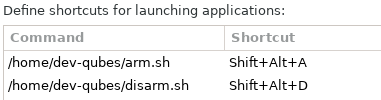
Auto arm on inserting yubikey
The purpose of the detect.sh file above is to automatically arm the system when your yubikey is inserted. This also works if you boot the system with the yubikey inserted.
Reboot your system
After rebooting your system your sys-usb qube will be created with all the changes we've made.
Your system is not currently armed.
The keyboard shortcut Alt+Shift+A will arm your system and you should get a notification confirming this. If you have a Yubikey inserted and remove it your system will shutdown
The keyboard shortcut Alt+Shift+D will disarm your system for 15 seconds. In this window you can attach your Yubikey to a different qube. After 15 seconds your system is armed again.Repeat if you need to attach your Yubikey to a different qube.
To permanently disarm your system just run the disarm-perm.sh script in dom0
Shortcomings of this approach
- Between the time you unlock your encrypted drive at boot and the time you arm the system after login you are exposed. If you login and forget to arm the system you will be exposed
- Before you attach your yubikey to a qube, you need to temporarily disable the buskill functionality
- You may accidentally shutdown system
- There are a lot of moving parts here and testing for your use cases is recommended.
- If you're just looking for protection then please go with the setup outlined by the creator https://www.buskill.in/qubes-os/
Cool things about this approach
- Yet another way to use your Yubikey
- Doesn't "waste" a USB slot as the Yubikey is still fully functional
- You get to learn all about udev and the neat things you can do with it


