Observing change can be a powerful tool. Automating that observation is even more powerful.
Today we'll have a look at "FBI Watchdog". This tool monitors sites for changes to their DNS records. Changes to DNS could be indicative of a law enforcement takeover amongst other things.
For a deeper dive into how and why I do these posts:
tl;dr What did I learn?
There is no shortage of premium enterprise level solutions that will monitor and alert on DNS for you. Some of them literally have "Domain" in the title, lol. You don't need to pay enterprise prices though. DNS is "all around us" and with an easy to use python library or two you can easily monitor for changes to a domain's DNS records.
It's as simple as asking "What does current state look like?" then repeatedly asking "Did anything change?".
Tool Details
- Author: DarkWebInformer
- Tool: https://github.com/DarkWebInformer/FBI_Watchdog
- Language: Python
- Requirements: dnspython, requests, python-dotenv, selenium, webdriver-manager, rich
Questions
- How is the tool checking for changes to DNS records?
- Can I disable notifications?
From previous posts, I've outlined my methodology as "Read their docs" -> "Understand dependencies" -> "Look for calls to external sites" -> "Ask AI".
Documentation
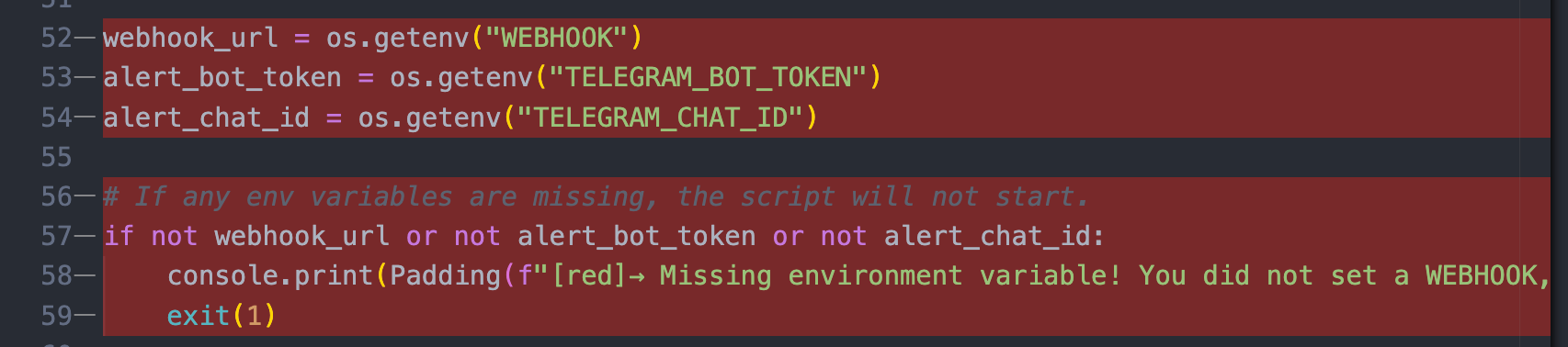
The README gives a good overview of what the tool does and how you need to set it up. From the docs we learn that we'll need to have some tokens set up before using the tool. This can be a barrier if you just want to try the tool out in the command line and don't care about notifications though.
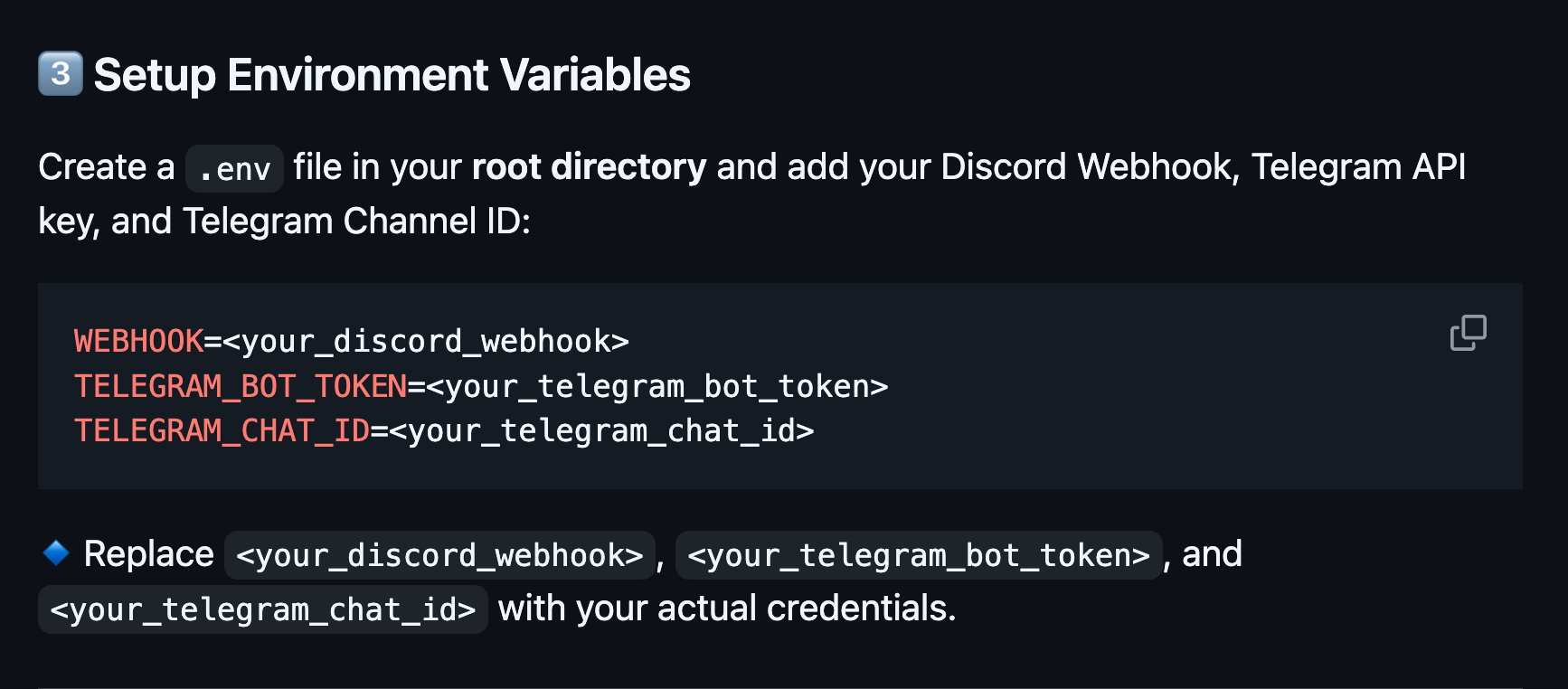
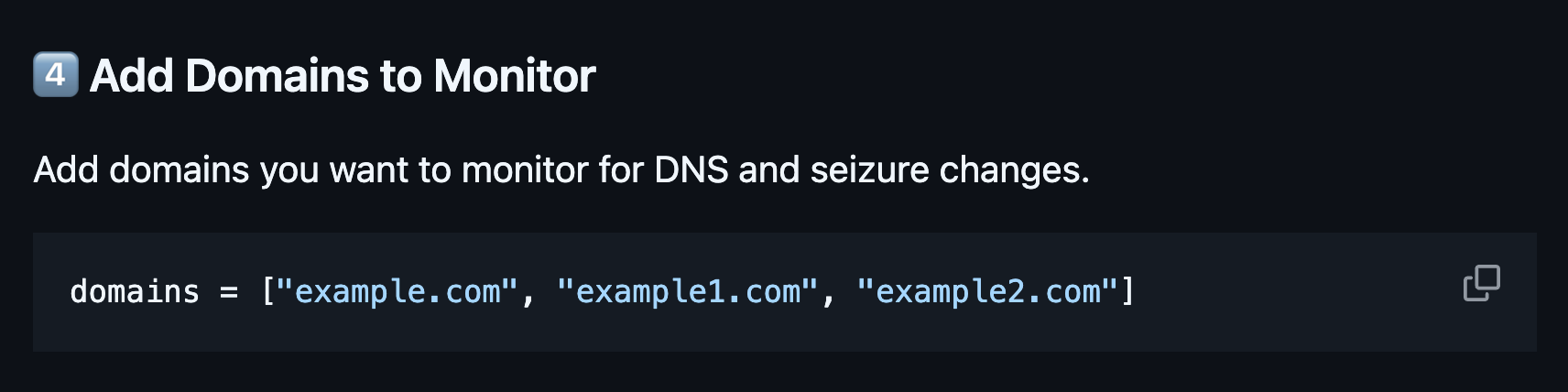
We learn that we'll need to supply a list of domain to monitor inside the python file. It does not come "pre-loaded" with a list of domains to watch
The inclusion of a Virus Total report link was an interesting touch. While coming up "clean" in VT shouldn't be the only consideration when running random code from the internet it's nice to see the developer reminding us to be skeptical even of them. I'll do a separate post about how to test open source tools safely.

Once your environment variables are set up, it really is as easy as running the python file.
Understand Dependencies
The inclusion of selenium , webdriver-manager and requests are all things I would expect after reading about the tool. The interesting one though is dnspython. TIL there is an entire python library for working with DNS records!
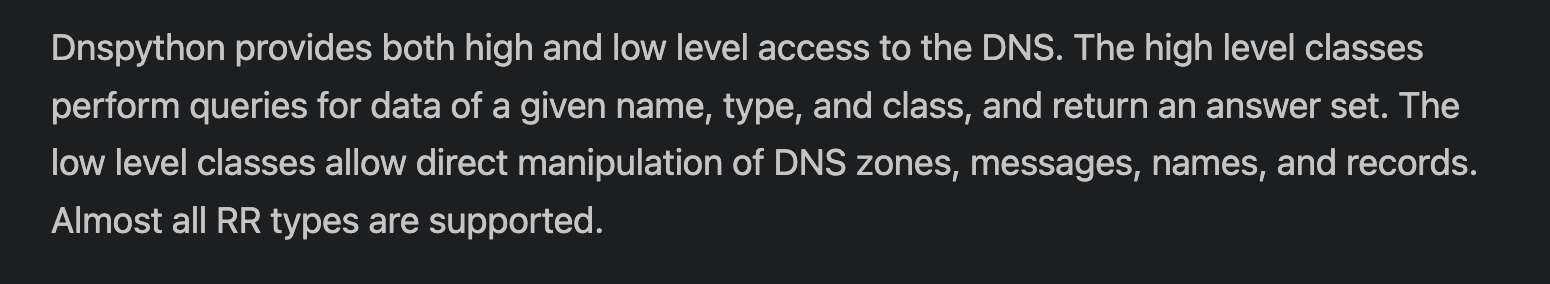
Now that we know about dnspython, the script is as simple as querying DNS records on a schedule and looking for changes compared to previous results.
Look for calls to external sites
This tool does not leverage any third party sites or APIs.
Question 1: How is the tool detecting changes to DNS records?
The dnspython library makes pulling DNS information very straightforward.
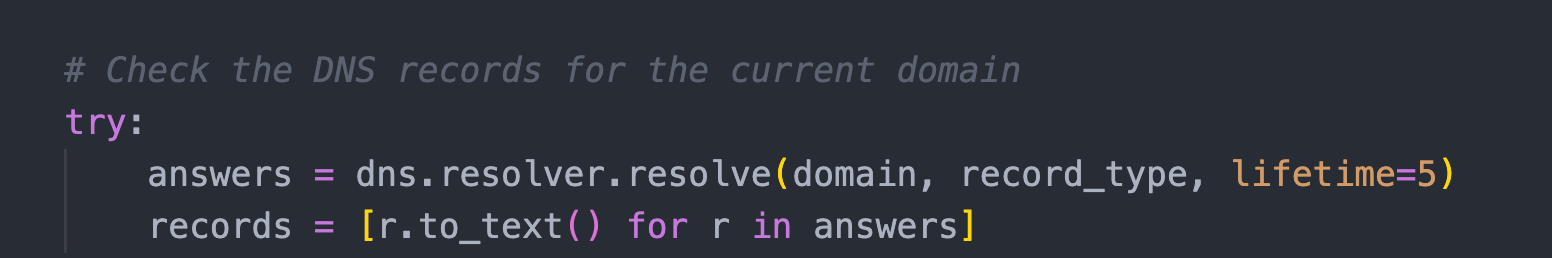
You need a methodology to store the records as you pull them
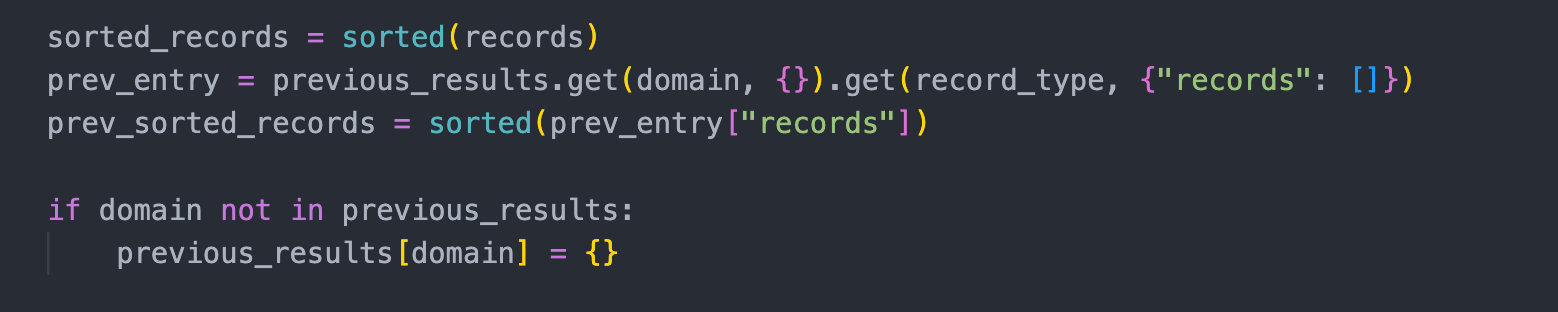
Then it's as simple as comparing your current results to previous results
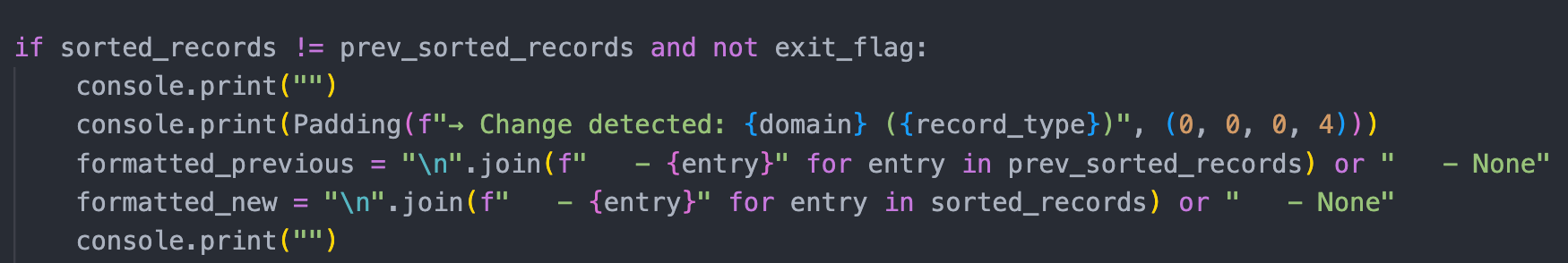
Question 2: Can I disable notifications?
Yep. If you only want to play with the tool on the command line and don't care about notifications it's as simple as commenting out the references to notifications:
Comment out the calls to discord_notify() and telegram_notify() towards the end of the script
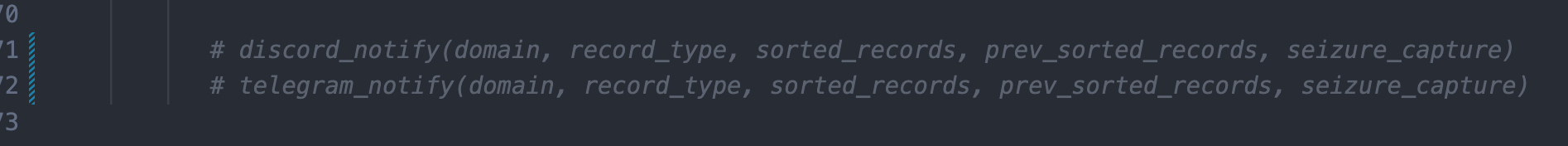
and remove the sections at the top that load up and check on the environment variables
Final Thoughts
This tool is a great example of "automate something you could do manually". I didn't touch on the notification piece but this tool is also a great example of the different free ways you can set up notifications in your own scripts as well.