I recently posted on LinkedIn about the importance of taking notes in the moment while attending talks and workshops at a conference. The thoughts and feelings you have during an event like that will be nearly impossible to accurately reproduce the longer times goes on. Trying to capture what's going on in your brain will pay dividends especially as time goes on.
You don't have to write an entire report just a few key thoughts, takeaways or followups that will aid you later. Once you get home and recover physically and emotionally I recommend creating a more structured document. This is my example.
This sounds a lot like school....
It can be a delicate balance between actually being present for the experience and trying to document it. This is why I advocate for a few keywords and observations that will jog your memory when you get home. Here's an example of a few notes I took on my phone via Obsidian:
Not exactly robust note taking but those were the things that resonated with me during those three talks. Your notes will not look like my notes. This is a personal process. After the conference, preferably a few days later, sit down to expand on those notes. Future You will appreciate it.
Final Product
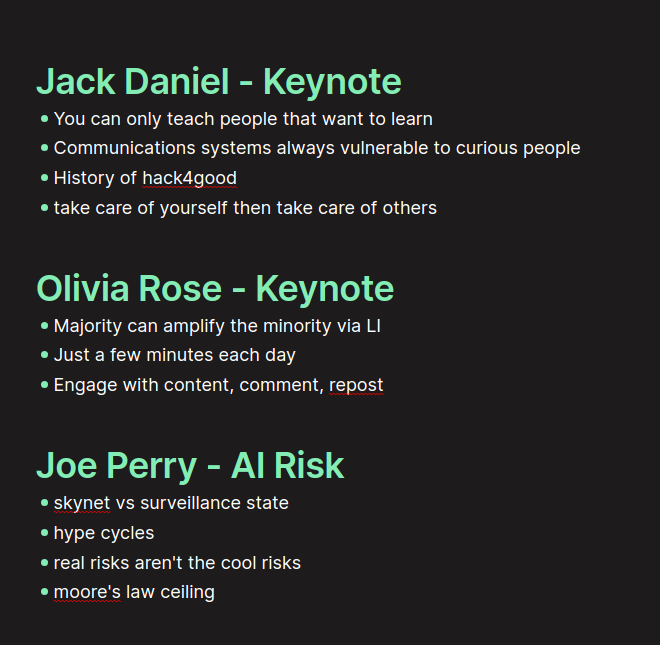
So the final product for my experiences at B Sides Bloomington will look something like this. This isn't a summary of the talks given but me talking through the things that resonated with me. Reading through this a month from now should make me think or feel similar things as I did at the con.
Jack Daniel Keynote
Jack's main messages were understanding the hackers that came before us and that any communication system can be tampered with given the right mix of motivation, resources and opportunity.
Also a picture in to what real hack4good looks like with the example of Rene Carmille, a French census bureau employee, who saved lives by altering or deleting certain census data the Nazis would use to track down Jewish people in France. He was ultimately executed for this actions.
Also that we need to take care of ourselves and take care of each other
Olivia Rose Keynote
Olivia's main message was that the majority can assist the minority simply by amplifying their voices on social media. Her example was engaging with content on LinkedIn. If the majority makes an effort to engage with minority produced content it will give amplification to their successes. This method doesn't require a lot of time and energy but does require the user to focus on doing it.
Generative AI and Business Risks with Joe Perry
There are two different "problems" with AI: Skynet and the surveillance state, it's only fun to talk about and solve for Skynet when we should be focusing on surveillance state. Talking about AI taking over the world is much easier than the work it would take to regulate the use of AI assisted tools in the wrong hands. Skynet is far less likely than governments and corporations using AI to monitor you more closely. Also talked through "hype cycles". These periods where some aspect of AI will be the "next big thing". Although these cycles come and go, they tend to leave some kind of lasting impression behind them. Also mentioning that AI is bound to the hardware it is running on and a physical cap to Moore's law could lead to a cap on AI development.
Enhancing Chrome Extension Security: Fortifying Your Browser Experience with Aishwarya Ramesh Nagarajan and Samuel Ogunlade
Great insight in to how extensions actually work and how we as users can see what they are up to, great explanation of v1, v2 and v3 extension rules and gave great examples of the different ways extensions can be abused : side loading, chrome store malicious and poorly written and taken advantage of by other sites.
Users installing extensions from outside the Chrome store are the most dangerous and likely most prevalent form of abuse. Also offered mitigations to put in place that can make it harder for users to make mistakes.
Forensics Lite with Nate Johnson
Came in halfway through. Showing all the investigating you can do with default Linux tools on a system. "no logs" means tampered logs, this was awesome to see what you can do with simple builtin tools. If logs are missing or smaller than you'd expect this can be bad. Also want to look for normally named files in strange files as well as hidden directories hiding in plain sight. Could compare the file system in front of you with a "regular" copy of a diff file system.
LLM Attacks and the OWASP Top 10 with Adam Cole
Went over the OWASP top 10 for LLMs and really focused in on overreliance on llm and overpermissioning. If we don't give AI access to making critical life altering decisions with no human oversight we should be in an pretty good place. Also, if we don't blindly trust it and instead use it to augment the work we are doing we should be in a safe place here as well.
Roll for Initiative with Kaleb Brown
Talked through the similarities between successful IR and successful TTRPGs. Things that both have in common: successful communication, both of these events require not only the people participating to have clear lines of communication but also the person orchestrating the entire event. Communication must also be continuous.
An understanding of your environment is key to both events. You can't run a game if you don't understand the world it takes place in and you can't do IR if you don't know your systems and your environment better than anyone else. You will be the expert in your world.
Cool story bro, so what?
Now you have a neat record of the impact your conference had on you. This could you give you jumping off points to other areas of study. For me, the talks I wrote the most about had the biggest impact on me and may be areas I want to dive deeper in to.


